Sumo Logic ahead of the pack
Read articleGuide
SOAR Guide
Security orchestration, automation and response – guide, tools and solutions.

What is SOAR?
SOAR (security, orchestration, automation and response) refers to software that allows organizations to streamline security operations across many areas, including threat and vulnerability management, incident response and security operations automation.
What does SOAR stand for?
SOAR is characterized by three key capabilities:
- Security orchestration: connecting security tools and integrating disparate security systems.
- Security automation: executing security operations-related tasks, such as retrieving new alerts, offenses and search results from security information and event management (SIEM) or indicators of compromise (IoCs) from threat intelligence, without human intervention.
- Security response: a structured multi-step process that allows organizations to avert or reduce the effects of cyberattacks and data breaches.
What is a SOAR system used for?
SOAR platforms and solutions work by collecting data from a variety of sources, such as log files, application metrics, and cloud monitoring services, and then analyzing that data to detect anomalies that could be signs of a breach. Then, SOARs help teams plan and execute a response strategy for the identified threats, speeding threat detection and remediation through automation.

With an effective SOAR solution, achieving more in less time is possible while still allowing for human decision-making when it’s most critical. SOAR helps teams move beyond relying on point-to-point integrations. Instead, SOAR tools build out various processes to connect the right people and technology to achieve goals.
Altogether, SOARs provide an end-to-end security solution for modern businesses.
How do you implement SOAR solutions?
A critical factor to the success of SOAR tools orchestration capabilities is having a library of plugins for the most-used technology and a set of pre-built workflows for common use cases.
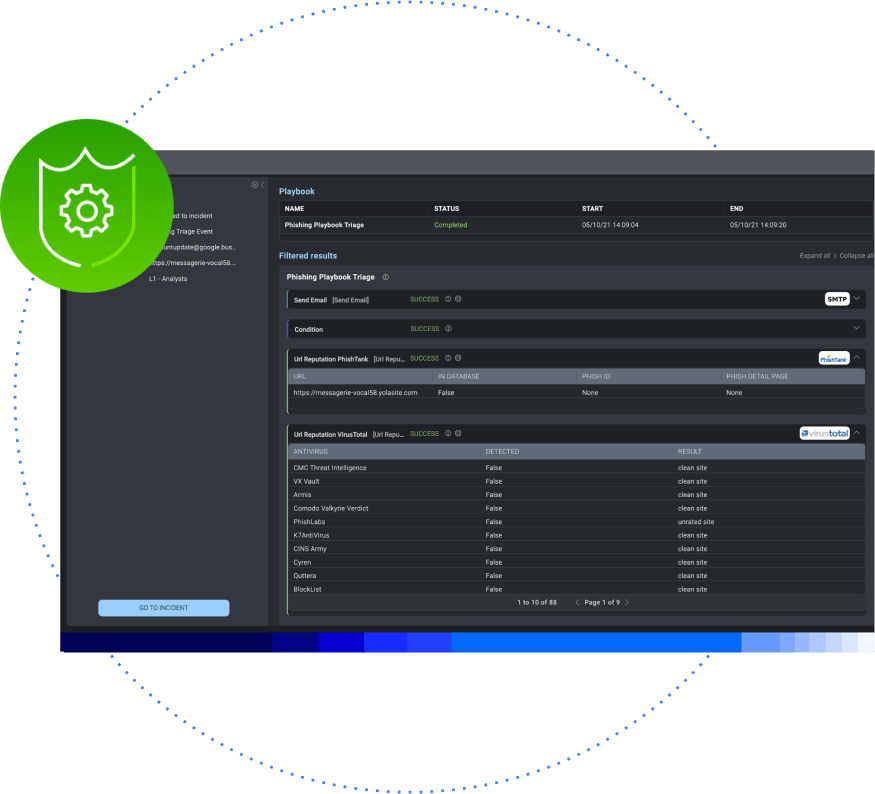
Typically, these workflows come in the form of customizable playbooks or runbooks based on industry standards and current best practices. They cover a broad spectrum of scenarios, from phishing to brute-forcing, to ransomware attacks. Equally important, playbooks allow you to automate a significant portion of the incident response lifecycle.

A wide range of plugins or integrations, along with pre-built playbooks, enables teams to easily connect your technology stack and automate your security and IT processes. You will likely need to build additional orchestrations or workflows customized to your team, but having pre-built examples and easy-to-use building blocks to work from should help accelerate the process.
The trends behind growing SOAR adoption
The term SOAR was coined by Gartner in 2017. According to analysts, SOAR adoption is growing rapidly due to three main factors.
The growing complexity of cybersecurity threats
Security threats are increasingly complex as attackers adopt techniques designed to obscure their activities. For example, they may use virtual machines to launch exploits, a practice that makes attacks harder to detect because metrics from the targeted machines don’t change until after the attack has already occurred. In other scenarios, malware may actively shut down a system’s security processes, preventing conventional security tools from discovering its presence.
As threats become more and more complex, SOARs provide deeper and more comprehensive security analytics to help diagnose and resolve threats faster. With a SOAR solution, companies can automatically collect more data and intensively analyze it to highlight threats and speed investigation activities.
>> Learn more: Overwhelmed: why SOAR solutions are a game-changer
The growing scale of cybersecurity threats and alerts
At the same time that threats are growing more complex, they are also increasingly pervasive. 2021 set records for the scope and frequency of cyberattacks, and 2023 is undoubtedly on track to do the same.
Subsequently, security teams have to respond to more alerts than ever. So-called alert fatigue is one of the most persistent challenges for security teams. They struggle to keep up with the volume of alerts and discern between false positives and negatives and which alerts to prioritize.

SOARs address these challenges by providing contextualized, actionable information about security threats from a variety of different tools. Instead of merely identifying risks, SOARs categorize them based on their threat level. In many cases, SOARs offer guidance on how teams can most efficiently respond to a threat. And as we’ve noted, SOARs can automatically remediate certain threats in some scenarios by orchestrating traditional security tools.
Cybersecurity skills shortage
Complicating the scale of modern threats is the fact that engineers qualified to respond to them are in short supply.
As of 2022, there were 435,000 unfilled cybersecurity positions in the United States, up from 314,000 in 2019. This “skill gap” is likely to get worse before it gets better.
Even the smallest cybersecurity teams can lean on SOAR tools to handle threats. SOAR automates complex security workflows while helping all necessary stakeholders to coordinate their security response activities.
>> Read the about the GigaOM Radar Report for SOAR solutions
The difference between SOAR and SIEM
SOAR is sometimes compared to SIEM. Generally, SIEM platforms:
Collect and aggregate logs from sources internal to a given IT environment, such as firewalls, databases, servers, applications, network appliances and intrusion detection systems (IDS)
Perform log auditing
Conduct real-time alert analysis
Create compliance reports
Can organizations replace SOAR with SIEM?
Historically, organizations have relied on SIEM to detect threats, but that’s where its functionality typically ends.
In contrast, SOAR orchestrates security responses to make threat intelligence actionable. With SOAR, you can coordinate disparate technologies — including third-party endpoint security providers, external threat intelligence feeds and other external tools to work together.
Many businesses leverage both for a more complete threat management solution.
Top benefits of SOAR solutions
SOAR helps build workflows and streamline operations
By adopting SOAR, businesses gain a variety of benefits that other types of security tools just don’t deliver.
Streamlined security response and automation
By making all data about security threats available to all stakeholders, and helping orchestrate response activities, SOAR eliminates the need to guess or take an ad hoc approach to threats.
In turn, SOAR helps to minimize the time it takes to contain and remediate threats – which is critical, given that active breaches can cost millions of dollars per minute.
SOAR provides enhanced alert management to help SOC teams
SOAR helps SOC teams make better sense of security alerts to improve their overall security posture. With a SOAR, it's possible to immediately see which systems are affected by a threat and determine the severity of a cyber threat without having to investigate it manually. It’s also easier to identify alerts that are likely false positives.
Usually, a legacy SIEM makes alert triage an arduous task carried out by security analysts handling an overwhelming number of alerts. Sifting through the incoming data to separate positives from false alerts, prioritizing alerts, converting them to incidents, prescribing the optimal incident response and coordinating incident response activities is incredibly time-consuming. Moreover, regardless of how diligent security analysts are, mistakes can happen, resulting in missed threats that cause havoc on organizations.
SOAR automation
One of the fundamental advantages of SOAR platforms is automating and orchestrating the triage process. SOARs can automatically deal with exabytes of data, employ a stack of tools, and unify diverse processes to sharpen decision-making and perform alert investigation, enrichment and threat detection. SOARs execute triage much faster and more efficiently than humans, especially if a machine learning engine powers the SOAR. The benefits of SOAR automation include:
Minimized false alerts and alert noise
Improved response time
Lower MTTR (Mean Time To Resolution) rates
Streamlined security incident response (through playbooks)
More efficient SecOps
In these ways, SOARs enable more efficient alert management. Rather than attempting to handle each security alert as it comes in, teams empowered with SOAR can react proactively and strategically based on the severity of each alert and the scope of affected resources.
SOAR can integrate disparate tool sets
SOARs are not a replacement for existing security tools, but they can help to unify them by serving as a centralized platform for collecting, analyzing, and reacting to security-related data.
Without a SOAR, you would likely need to juggle a slew of different tools – such as log aggregators, metrics collection services, SIEM, threat intelligence, firewalls, IDS, IPS, EDR, IT services, ticketing system, IAM, analytics and monitoring, sandbox, XDR, email and web gateway, proxy, URL filtering, vulnerability management, IoT Monitoring, CASB, OT security tools, and so on – to stay on top of security threats. A SOAR functions as a common connector for all these tools, allowing you to centralize security operations around a single platform.
Lower costs with SOAR systems
Ultimately, SOARs can lower costs in two ways.
First, they reduce the time engineers spend manually identifying and responding to security threats. This translates to lower staffing costs.
Second, by reducing the time it takes to contain and remediate a breach, SOARs can help minimize the financial impact of cybersecurity events. SOAR platforms also help to reduce the amount of data exposed during a breach, which protects business reputation and may help to avoid regulatory fines. It’s commonly thought that cybersecurity teams are the only ones responsible for cyber attacks, but this is not true. Cybersecurity awareness has room for improvement. Every department that develops projects without considering cybersecurity puts its entire company at risk.
Increased flexibility, extensibility and collaboration across security teams
Although security teams may be the primary users of a SOAR, security analysts alone can rarely remediate an issue. Chances are, an organization uses technology multiple teams need to touch and collaborate on, yet the various pieces don’t always integrate. For example, if the root cause of a threat is a code vulnerability, they will need to work with developers to fix it. If it’s a configuration issue with an application or cloud service, they’ll need help from IT engineers. SOARs ensure that developers, IT engineers and other groups who need to be looped into the process can collaborate readily to achieve a speedy, effective response tracking every phase and related time.
Choosing the best SOAR solution
Whether you’re new to SOAR or you’re looking to change your current SOAR vendor, it’s important to align the needs of your security operations teams with the right SOAR solution. Since SOAR can significantly impact the security operations center (SOC), it is essential to understand the available options to make the best decision for the right SOAR solution. Whether adapting workflows, creating and managing integrations, or building entirely new processes, it’s essential to understand how to compare SOAR solutions and vendors. Here are the criteria for finding the best SOAR solution:
Allows easy and flexible creation of bidirectional integrations.
Supports common methods of data ingestion, such as Syslog, database connections, APIs, email, online forms, and data standards such as CEF, OpenIOC and STIX/TAXII.
Incorporates easy-to-build workflows by adding actions into playbooks to define standard operating procedures (SOPs) without programming knowledge.
Includes additional features to manage the complete incident response and management lifecycles, such as tracking cases, recording actions taken during the incident, and reporting critical metrics and KPIs.
Orchestrates and automates many different kinds of threat intelligence.
Supports multiple instances on a single host, providing accurate data segregation and access controls for each tenant’s information.
Why businesses choose Sumo Logic Cloud SOAR
There are a variety of vendors offering solutions labeled as SOAR. For guidance on the SOAR market, check out our SOAR buyer’s guide. Some are mostly SIEM platforms with some basic SOAR functionality tacked on. Others are SOAR solutions that only work in specific environments or with certain types of infrastructure.
Sumo Logic Cloud SOAR is built from the ground up to deliver complete SOAR functionality in any type of environment — private cloud, single cloud, multi-cloud or hybrid cloud. Here’s a chart that summarizes the comparison with Sumo Logic Cloud SOAR:
Actions | Without Sumo Logic | With Sumo Logic |
Incident assignment | Incidents are assigned through the ticketing system by manually collecting information from different tools. The resulting analysis of the information collected will not be straightforward. | Sumo Logic Cloud SOAR automatically creates incidents only when real threats are detected and assigns them to a specific analyst or group of analysts. Incidents in the Case Manager are enriched with all the essential information, enabling the SOC team to immediately and transparently collaborate, and support better case management. |
Playbook activation | If the SOC team has written incident response procedures, they have to follow them by managing several tool interfaces. If they lack these pre-determined procedures, the individuals often improvise based on their experience and skills. | Sumo Logic Cloud SOAR automatically generates playbook recommendations based on the type of alert. This helps security analysts to activate the correct standard operating procedures and tasks for the specific situation. This also enables the SOC team to scale their response capabilities and improve reaction time. |
Standard operating procedure task management | The SOC team must manage different features across separate tools and follow written instructions (if they exist). | Sumo Logic Cloud SOAR orchestrates the SOC team’s entire security stack and automates time-consuming tasks through progressive automation. This allows users to dictate how they automate their standard response processes. |
Report creation | Analysts have to collect all pertinent information and build a report manually. | Sumo Logic Cloud SOAR automatically creates detailed incident reports for the SOC team. |
How the University of California, Davis accelerates threat response with Cloud SOAR
Catering to researchers, students, faculty, and staff, UC Davis systems generate 10,000 events per second. Adding to its security challenges, UC Davis runs on open access policies and has a federated IT governance model working throughout its campus.
To automate some processes in their security operations, the SOC team has developed an API-centric scripting model supported by student-developed Python scripts, but it leaves some security gaps. UC Davis uses Sumo Logic Cloud SOAR to help accelerate its threat response and improve the efficiency of its SOC with a hybrid cloud architecture.
Cloud SOAR’s Open Integration Framework makes it compatible with the SOC’s preexisting Python scripts, sparing the team from building new integrations. Not only does Cloud SOAR supply the missing piece in the SOC workflow, integrating with all the existing technologies they use, but it also satisfies their security requirements.
With Cloud SOAR, UC Davis supports research and ensures security policies and procedures to protect itself from potential attacks.
Experience Cloud SOAR
Sumo Logic Cloud SOAR lets security teams work efficiently and proactively, no matter how many alerts they have to juggle, which other security tools they need to connect to their SOAR or which types of security threats they face.
Sumo Logic Cloud SOAR relies on its Open Integration Framework to easily blend within the deployed environment and integrate with different security technologies seamlessly, including SIEM. Instead of maneuvering between multiple dashboards, Cloud SOAR uses detailed case (incident) information — from identification to remediation — in a single dashboard. This allows security teams to build and maintain their incident response processes with full visibility and harmoniously utilize Cloud SOAR and Cloud SIEM.
See how Cloud SOAR can quickly become an integral part of your infrastructure — request a demo of Sumo Logic Cloud SOAR.

